Password cracking Wikipedia. In cryptanalysis and computer security, password cracking is the process of recovering passwords from data that have been stored in or transmitted by a computer system. A common approach brute force attack is to try guesses repeatedly for the password and check them against an available cryptographic hash of the password. The purpose of password cracking might be to help a user recover a forgotten password installing an entirely new password is less of a security risk, but it involves System Administration privileges, to gain unauthorized access to a system, or as a preventive measure by system administrators to check for easily crackable passwords. On a file by file basis, password cracking is utilized to gain access to digital evidence for which a judge has allowed access but the particular files access is restricted. Cain And Abel Hack Software' title='Cain And Abel Hack Software' />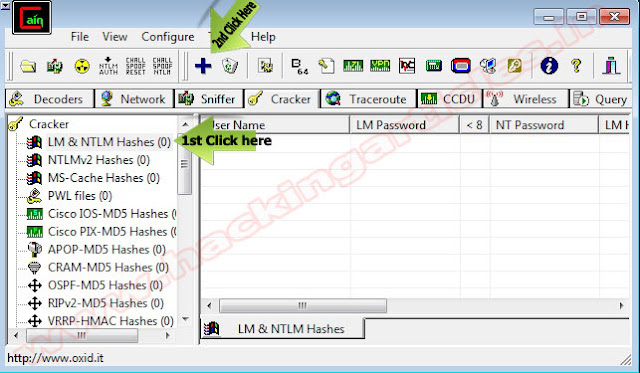 Time needed for password searcheseditThe time to crack a password is related to bit strength seepassword strength, which is a measure of the passwords entropy, and the details of how the password is stored. Most methods of password cracking require the computer to produce many candidate passwords, each of which is checked. One example is brute force cracking, in which a computer tries every possible key or password until it succeeds. More common methods of password cracking, such as dictionary attacks, pattern checking, word list substitution, etc. Higher password bit strength exponentially increases the number of candidate passwords that must be checked, on average, to recover the password and reduces the likelihood that the password will be found in any cracking dictionary. The ability to crack passwords using computer programs is also a function of the number of possible passwords per second which can be checked. If a hash of the target password is available to the attacker, this number can be quite large. If not, the rate depends on whether the authentication software limits how often a password can be tried, either by time delays, CAPTCHAs, or forced lockouts after some number of failed attempts. Cain and Abel. Cain and Abel is a wellknown password cracking tool that is capable of handling a variety of tasks. The most notable thing is that the tool is only. Cain and abel is one of best Tool that is commonly used to Poison the network or Do a man in middle Attack in the whole Network. But According to the Oxid. Another situation where quick guessing is possible is when the password is used to form a cryptographic key. In such cases, an attacker can quickly check to see if a guessed password successfully decodes encrypted data. For some kinds of password hash, ordinary desktop computers can test over a hundred million passwords per second using password cracking tools running on a general purpose CPU and billions of passwords per second using GPU based password cracking tools. See John the Ripper benchmarks. The rate of password guessing depends heavily on the cryptographic function used by the system to generate password hashes. A suitable password hashing function, such as bcrypt, is many orders of magnitude better than a naive function like simple MD5 or SHA. A user selected eight character password with numbers, mixed case, and symbols, with commonly selected passwords and other dictionary matches filtered out, reaches an estimated 3. NIST. 2. 30 is only one billion permutations7 and would be cracked in seconds if the hashing function is naive. When ordinary desktop computers are combined in a cracking effort, as can be done with botnets, the capabilities of password cracking are considerably extended. Magical Jelly Bean Keyfinder 2. Englisch. Das Tool Magical Jelly Bean Keyfinder liest Ihnen Ihre eigenen LizenzSchlssel von Windows und anderer Software aus. That is what you call a hack C,mon a hack is a lot more sophisticated. Why dont you tell people how to HACK or tell them how to cover there IP address using. Cain-Abel-NTLM.png' alt='Cain And Abel Hack Software' title='Cain And Abel Hack Software' />Wir stellen Ihnen 20 HackerTools vor, die von Profis genutzt werden. Darunter finden Sie auch Programme, die sich zu illegalen Zwecken mibrauchen lassen. Bei. http Facebook penetration penetrating a. Biggest list of free hacking tools for you to hack proficiently. In 2. 00. 2, distributed. Bubble Puzzle Game Free Download. RC5 key in four years, in an effort which included over 3. Graphics processors can speed up password cracking by a factor of 5. As of 2. 01. 1, available commercial products claim the ability to test up to 2,8. Such a device can crack a 1. The work can be distributed over many computers for an additional speedup proportional to the number of available computers with comparable GPUs. Despite their capabilities, desktop CPUs are slower at cracking passwords than purpose built password breaking machines. In 1. 99. 8, the Electronic Frontier Foundation EFF built a dedicated password cracker using ASICs, as opposed to general purpose CPUs. Their machine, Deep Crack, broke a DES 5. In 2. 01. 0, the Georgia Tech Research Institute developed a method of using GPGPU to crack passwords, coming up with a minimum secure password length of 1. Penetration testing The complete guide with top 37 Penetration Testing Tools every Penetration tester should know. Tools review with download link. Easy to remember, hard to guesseditA password that is easy to remember is generally also easy for an attacker to guess. Passwords that are difficult to remember will reduce the security of a system because a users might need to write down or electronically store the password using an insecure method, b users will need frequent password resets and c users are more likely to re use the same password. Similarly, the more stringent requirements for password strength, e. In The Memorability and Security of Passwords,1. Jeff Yan et al. examines the effect of advice given to users about a good choice of password. They found that passwords based on thinking of a phrase and taking the first letter of each word are just as memorable as naively selected passwords, and just as hard to crack as randomly generated passwords. Combining two unrelated words is another good method. Having a personally designed Algorithm for generating obscure passwords is another good method. In the latest improvements, more and more people are noticing change in the way that passwords are secured. However, asking users to remember a password consisting of a mix of uppercase and lowercase characters is similar to asking them to remember a sequence of bits hard to remember, and only a little bit harder to crack e. Asking users to use both letters and digits will often lead to easy to guess substitutions such as E 3 and I 1, substitutions which are well known to attackers. Similarly typing the password one keyboard row higher is a common trick known to attackers. Research detailed in an April 2. Carnegie Mellon University shows that peoples choices of password structure often follow several known patterns. As a result, passwords may be much more easily cracked than their mathematical probabilities would otherwise indicate. Passwords containing one digit, for example, disproportionately include it at the end of the password. IncidentseditOn July 1. CERT reported an incident where an attacker had found 1. By the time they were discovered, they had already cracked 4. In December 2. 00. Rockyou. com website occurred that led to the release of 3. The attacker then leaked the full list of the 3. Passwords were stored in cleartext in the database and were extracted through a SQL Injection vulnerability. The Imperva Application Defense Center ADC did an analysis on the strength of the passwords. In June 2. 01. 1, NATO North Atlantic Treaty Organization experienced a security breach that led to the public release of first and last names, usernames, and passwords for more than 1. The data were leaked as part of Operation Anti. Sec, a movement that includes Anonymous, Lulz. Sec, as well as other hacking groups and individuals. On July 1. 1, 2. 01. Booz Allen Hamilton, a large American Consulting firm that does a substantial amount of work for the Pentagon, had their servers hacked by Anonymous and leaked the same day. The leak, dubbed Military Meltdown Monday, includes 9. USCENTCOM, SOCOM, the Marine Corps, various Air Force facilities, Homeland Security, State Department staff, and what looks like private sector contractors. These leaked passwords wound up being hashed in Sha.
Time needed for password searcheseditThe time to crack a password is related to bit strength seepassword strength, which is a measure of the passwords entropy, and the details of how the password is stored. Most methods of password cracking require the computer to produce many candidate passwords, each of which is checked. One example is brute force cracking, in which a computer tries every possible key or password until it succeeds. More common methods of password cracking, such as dictionary attacks, pattern checking, word list substitution, etc. Higher password bit strength exponentially increases the number of candidate passwords that must be checked, on average, to recover the password and reduces the likelihood that the password will be found in any cracking dictionary. The ability to crack passwords using computer programs is also a function of the number of possible passwords per second which can be checked. If a hash of the target password is available to the attacker, this number can be quite large. If not, the rate depends on whether the authentication software limits how often a password can be tried, either by time delays, CAPTCHAs, or forced lockouts after some number of failed attempts. Cain and Abel. Cain and Abel is a wellknown password cracking tool that is capable of handling a variety of tasks. The most notable thing is that the tool is only. Cain and abel is one of best Tool that is commonly used to Poison the network or Do a man in middle Attack in the whole Network. But According to the Oxid. Another situation where quick guessing is possible is when the password is used to form a cryptographic key. In such cases, an attacker can quickly check to see if a guessed password successfully decodes encrypted data. For some kinds of password hash, ordinary desktop computers can test over a hundred million passwords per second using password cracking tools running on a general purpose CPU and billions of passwords per second using GPU based password cracking tools. See John the Ripper benchmarks. The rate of password guessing depends heavily on the cryptographic function used by the system to generate password hashes. A suitable password hashing function, such as bcrypt, is many orders of magnitude better than a naive function like simple MD5 or SHA. A user selected eight character password with numbers, mixed case, and symbols, with commonly selected passwords and other dictionary matches filtered out, reaches an estimated 3. NIST. 2. 30 is only one billion permutations7 and would be cracked in seconds if the hashing function is naive. When ordinary desktop computers are combined in a cracking effort, as can be done with botnets, the capabilities of password cracking are considerably extended. Magical Jelly Bean Keyfinder 2. Englisch. Das Tool Magical Jelly Bean Keyfinder liest Ihnen Ihre eigenen LizenzSchlssel von Windows und anderer Software aus. That is what you call a hack C,mon a hack is a lot more sophisticated. Why dont you tell people how to HACK or tell them how to cover there IP address using. Cain-Abel-NTLM.png' alt='Cain And Abel Hack Software' title='Cain And Abel Hack Software' />Wir stellen Ihnen 20 HackerTools vor, die von Profis genutzt werden. Darunter finden Sie auch Programme, die sich zu illegalen Zwecken mibrauchen lassen. Bei. http Facebook penetration penetrating a. Biggest list of free hacking tools for you to hack proficiently. In 2. 00. 2, distributed. Bubble Puzzle Game Free Download. RC5 key in four years, in an effort which included over 3. Graphics processors can speed up password cracking by a factor of 5. As of 2. 01. 1, available commercial products claim the ability to test up to 2,8. Such a device can crack a 1. The work can be distributed over many computers for an additional speedup proportional to the number of available computers with comparable GPUs. Despite their capabilities, desktop CPUs are slower at cracking passwords than purpose built password breaking machines. In 1. 99. 8, the Electronic Frontier Foundation EFF built a dedicated password cracker using ASICs, as opposed to general purpose CPUs. Their machine, Deep Crack, broke a DES 5. In 2. 01. 0, the Georgia Tech Research Institute developed a method of using GPGPU to crack passwords, coming up with a minimum secure password length of 1. Penetration testing The complete guide with top 37 Penetration Testing Tools every Penetration tester should know. Tools review with download link. Easy to remember, hard to guesseditA password that is easy to remember is generally also easy for an attacker to guess. Passwords that are difficult to remember will reduce the security of a system because a users might need to write down or electronically store the password using an insecure method, b users will need frequent password resets and c users are more likely to re use the same password. Similarly, the more stringent requirements for password strength, e. In The Memorability and Security of Passwords,1. Jeff Yan et al. examines the effect of advice given to users about a good choice of password. They found that passwords based on thinking of a phrase and taking the first letter of each word are just as memorable as naively selected passwords, and just as hard to crack as randomly generated passwords. Combining two unrelated words is another good method. Having a personally designed Algorithm for generating obscure passwords is another good method. In the latest improvements, more and more people are noticing change in the way that passwords are secured. However, asking users to remember a password consisting of a mix of uppercase and lowercase characters is similar to asking them to remember a sequence of bits hard to remember, and only a little bit harder to crack e. Asking users to use both letters and digits will often lead to easy to guess substitutions such as E 3 and I 1, substitutions which are well known to attackers. Similarly typing the password one keyboard row higher is a common trick known to attackers. Research detailed in an April 2. Carnegie Mellon University shows that peoples choices of password structure often follow several known patterns. As a result, passwords may be much more easily cracked than their mathematical probabilities would otherwise indicate. Passwords containing one digit, for example, disproportionately include it at the end of the password. IncidentseditOn July 1. CERT reported an incident where an attacker had found 1. By the time they were discovered, they had already cracked 4. In December 2. 00. Rockyou. com website occurred that led to the release of 3. The attacker then leaked the full list of the 3. Passwords were stored in cleartext in the database and were extracted through a SQL Injection vulnerability. The Imperva Application Defense Center ADC did an analysis on the strength of the passwords. In June 2. 01. 1, NATO North Atlantic Treaty Organization experienced a security breach that led to the public release of first and last names, usernames, and passwords for more than 1. The data were leaked as part of Operation Anti. Sec, a movement that includes Anonymous, Lulz. Sec, as well as other hacking groups and individuals. On July 1. 1, 2. 01. Booz Allen Hamilton, a large American Consulting firm that does a substantial amount of work for the Pentagon, had their servers hacked by Anonymous and leaked the same day. The leak, dubbed Military Meltdown Monday, includes 9. USCENTCOM, SOCOM, the Marine Corps, various Air Force facilities, Homeland Security, State Department staff, and what looks like private sector contractors. These leaked passwords wound up being hashed in Sha.
New Posts
- How To Update Your Ps2 Software Games
- Update Nissan Navigation System Australia Immigration
- Canon Eos 1D Mark Ii N Software
- How To Install A Hot Water Tank
- Patch Alien Shooter 2 Conscription Unlock
- Best Software For Live Looping Software
- For The Love Of The Click 1997 Download Movies
- Belkin Wireless Ethernet Bridge Software For Ipad
- Out Of The Silent Planet Book
- Test Drive Unlimited Crack Online Rocket